The Protocol (LWM-Auth-V2.0)
(The first version of this protocol is published in ISCAS 2024.)
The PUF-based authentication protocol is designed with a two-step process. First is the device registration, and the second is the authentication or mutual authentication or mutual authentication and key agreement.
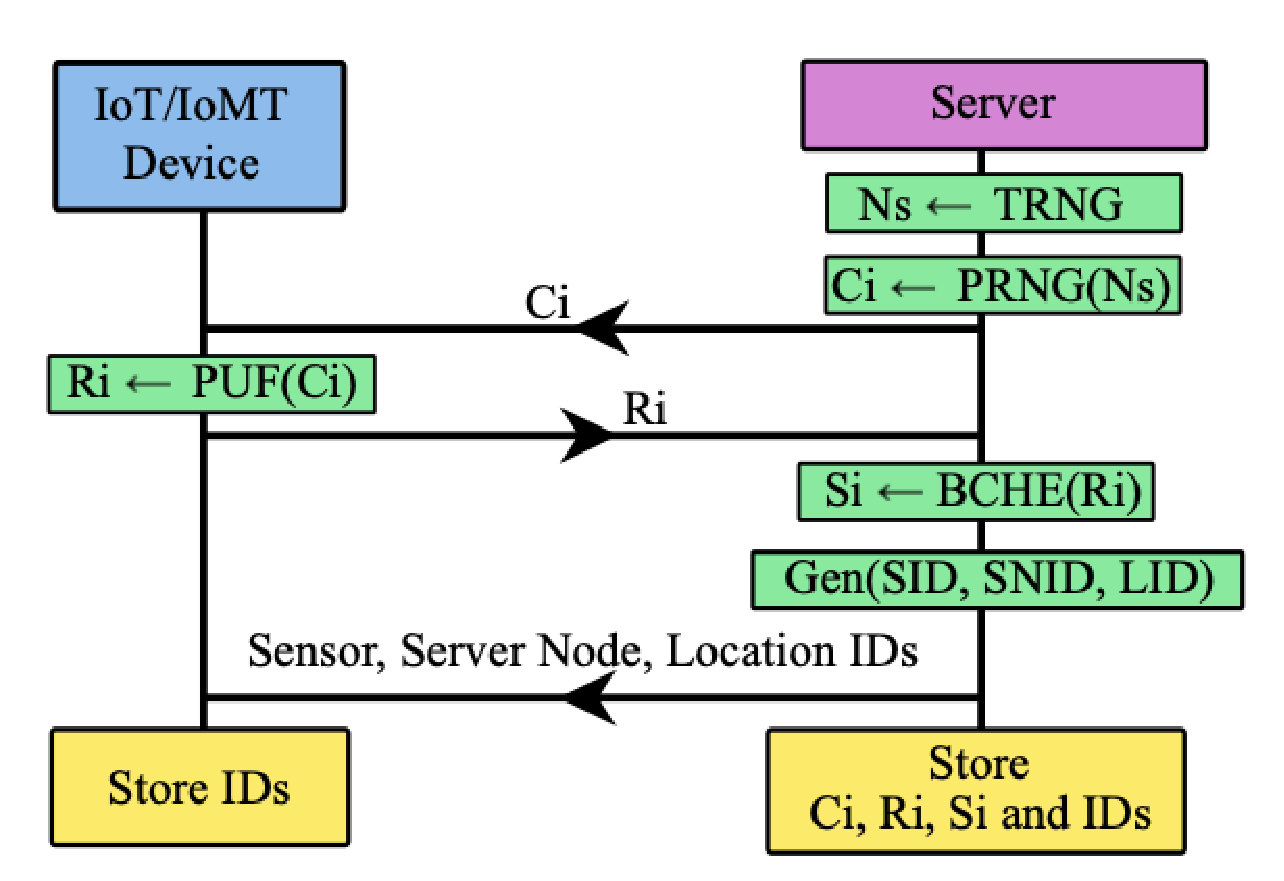
Device Registration
For successful mutual authentication, both devices should know the same secret. The device registration process involves sharing secrets (which is PUF CRPs) with the host server or PC in a secure environment. After device registration, the devices are deployed in the production environment.
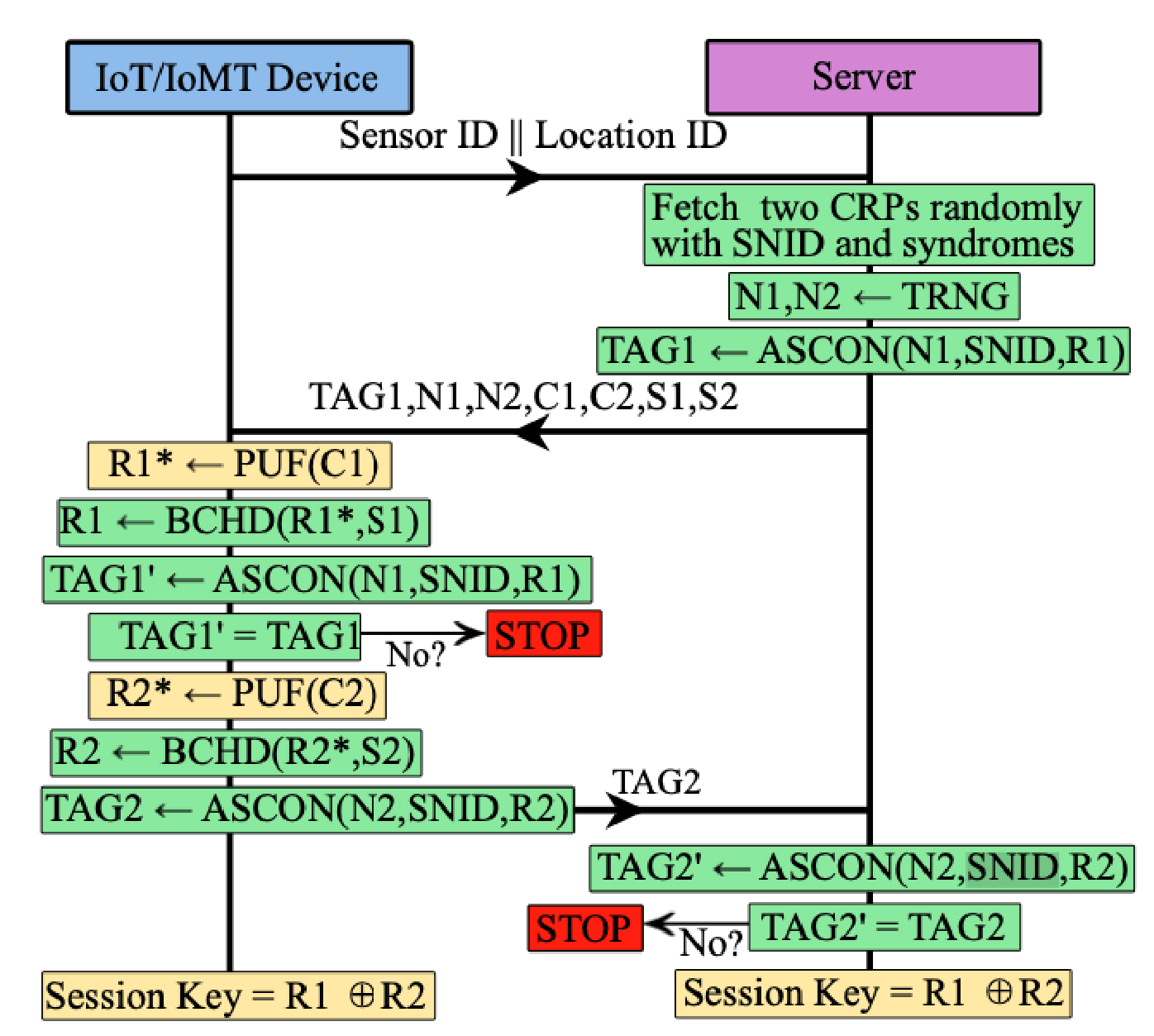
Mutual Authentication and Key Agreement
This process is executed whenever the devices need access to the public network to exchange sensitive data, or the session key needs to be updated.
The detailed description of the first version of the protocol is available in this link.
Last Update: 13 Sept 2025